File signatures by header: https://www.garykessler.net/library/file_sigs.html
ASCII tables: https://www.asciitable.com/ https://www.rapidtables.com/code/text/ascii-table.html
COFF:
IMAGE_NT_HEADERS32 Structure:
https://documentation.help/DbgHelp/image_nt_headers_str.htm https://learn.microsoft.com/en-us/windows/win32/api/winnt/ns-winnt-image_nt_headers32
IMAGE_NT_HEADERS64 Structure:
https://documentation.help/DbgHelp/image_nt_headers_str.htm https://learn.microsoft.com/en-us/windows/win32/api/winnt/ns-winnt-image_nt_headers64
PE format: https://learn.microsoft.com/en-us/windows/win32/debug/pe-format
Important "Optional" Header Field:
Signature - PE32 or PE32+
AddressOfEntryPoint - relative address to image base, where execution starts from
ImageBase - Preferred address of the first byte of image when loaded into memory - must be a multiple of 64k
SectionAlignment - alignment of sections when they are loaded into memory, mustbe greater than or equal to File alignment
FileAlignment - alignment factor, used to align raw data of sections in image file. If SectionAlignment is < than the architecture's page size then FileAlignment must match SectionAlignment
MajorOperatingSystemVersion
SizeOfImage
Subsystem
DLLCharacteristics
Important DLLCharacteristics:
IMAGE_DLLCHARACTERISTICS_DYNAMIC_BASE - DLL could be relocated at load time
IMAGE_DLLCHARACTERISTICS_FORCE_INTEGRITY - Code Integrity checks are enforced
IMAGE_DLLCHARACTERISTICS_NX_COMPAT - img is compatible w/ data Execution prevention (DEP)
IMAGE_DLLCHARACTERISTICS_NO_SEH - img does not use structured exception handling (SEH) which is used by windows for exception handling
IMAGE_DLLCHARACTERISTICS_TERMINAL_SERVER_AWARE - img is terminal server aware
Address Equations - All depends where the Image Base is loaded
VA = ImageBase + RVA
RVA = VA - ImageBase
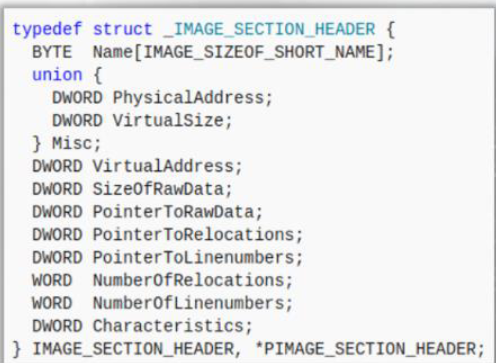
IMAGE_SECTION_HEADER:
Memory Characteristics = section contains code, read/write perms
.rdata/idata - import info or read only initialized data is located
Debug Directory - may contain useful info for IOCs, program's debug information
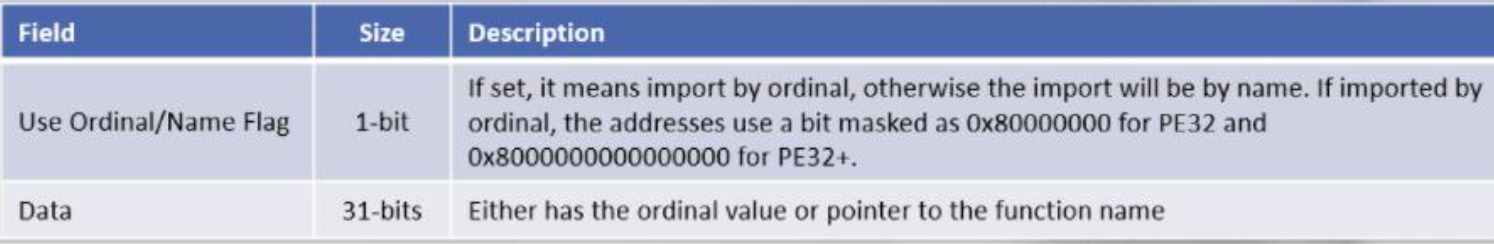
Import Directory Table - Structure for every imported library:
ImportLookupTable- 4 byte record:
Grab Memory:
MemDump
Dumpit https://www.comae.com/dumpit/
KAPE https://www.kroll.com/en/services/cyber-risk/incident-response-litigation-support/kroll-artifact-parser-extractor-kape
Fuzzy Hash: SSDEEP: https://ssdeep-project.github.io/ssdeep/index.html
Strings - Windows
Bstrings: https://github.com/EricZimmerman/bstrings / https://ericzimmerman.github.io/#!index.md
BinText - http://b2b-download.mcafee.com/products/tools/foundstone/bintext303.zip
StringSifter - https://github.com/mandiant/stringsifter pip install stringsifter
FLOSS - https://github.com/mandiant/flare-floss
API Obfuscation
DiE - https://github.com/horsicq/Detect-It-Easy
PEiD - https://github.com/packing-box/peid
Cuckoo = https://docs.cuckoosandbox.org/en/latest/
Anlyz - https://sandbox.anlyz.io/
Comodo Valkryie - https://valkyrie.comodo.com/
Falcon - https://hybrid-analysis.com/
VirusTotal - https://www.virustotal.com/gui/home/upload
Registers: https://www.eecg.utoronto.ca/~amza/www.mindsec.com/files/x86regs.html
Assembly Tester: https://defuse.ca/online-x86-assembler.htm
Compile and edit code: https://godbolt.org
https://malwareanalysis.co/cheat-sheets/
https://www.sans.org/blog/4-cheat-sheets-for-malware-analysis/
https://gbhackers.com/malware-analysis-cheat-sheet-and-tools-list/
https://lnkd.in/dfB9uHFt
https://zeltser.com/malware-sample-sources/
https://malapi.io/